Créer un groupe de sécurité
Depuis l'interface
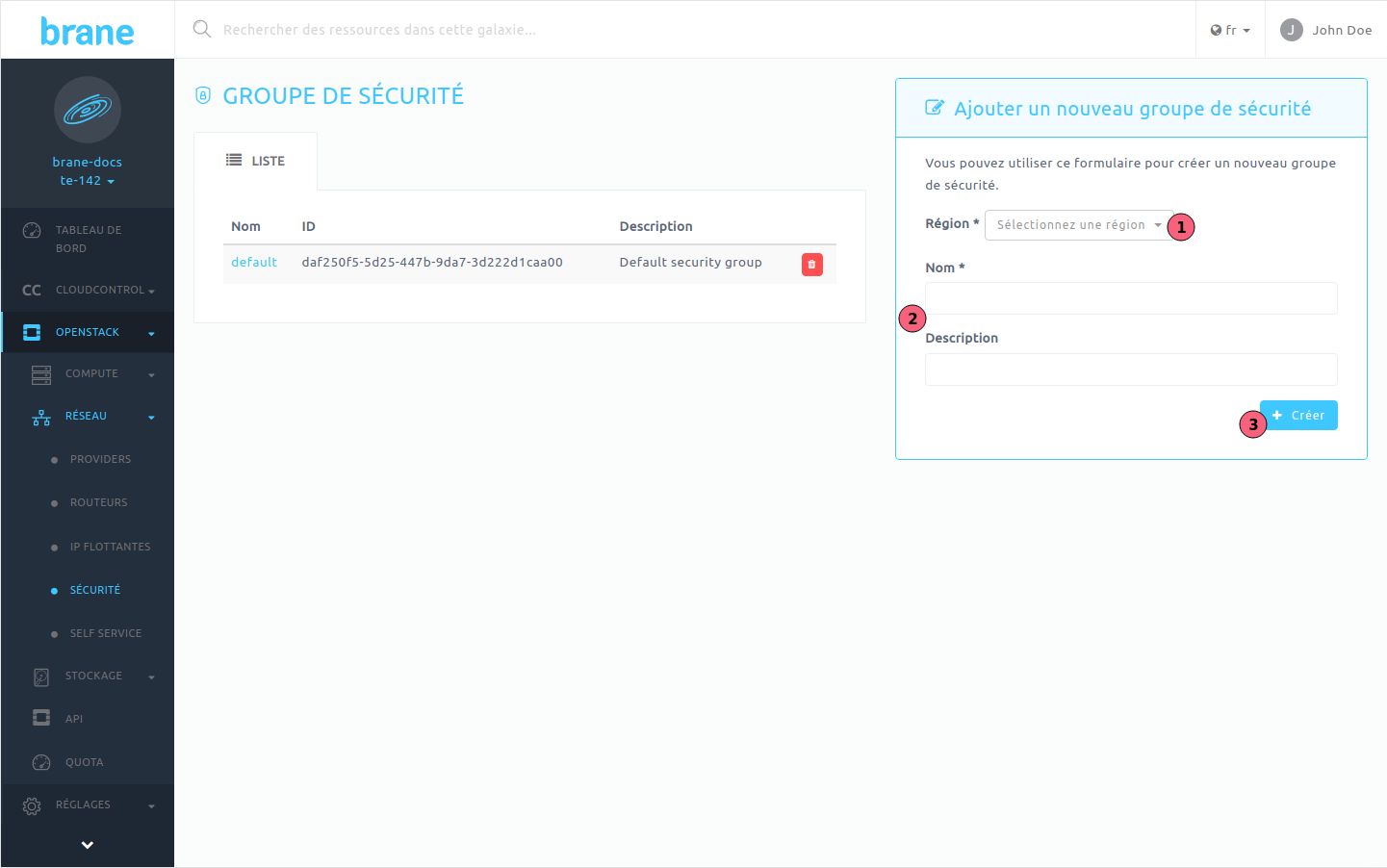
- Sélectionner la région dans laquelle créer le groupe ;
- Remplir les informations permettant l'identification du groupe (la description est optionnelle) ;
- Cliquer sur le bouton "Créer" .
Depuis la CLI
$ openstack security group create [--description "<...>"] [--stateful | --stateless] <name>
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+
| Field | Value |
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+
| created_at | 2021-09-30T09:15:01Z |
| description | Autoriser le SSH |
| id | b3d551ef-bb0d-4280-b6b7-2bcfdb198d02 |
| name | OpenSSH |
| project_id | 3a5e96cb73d24c7b981be504d8adcf88 |
| revision_number | 1 |
| rules | created_at='2021-09-30T09:15:01Z', direction='egress', ethertype='IPv4', id='265eb273-564b-4196-bf35-f5deb2e0bcf9', updated_at='2021-09-30T09:15:01Z' |
| | created_at='2021-09-30T09:15:01Z', direction='egress', ethertype='IPv6', id='4ce02fcb-dd05-49e4-8243-2ab250c2bbf4', updated_at='2021-09-30T09:15:01Z' |
| stateful | True |
| tags | [] |
| updated_at | 2021-09-30T09:15:01Z |
+-----------------+-------------------------------------------------------------------------------------------------------------------------------------------------------+
resource "openstack_compute_secgroup_v2" "secgroup_1" {
name = "OpenSSH_HTTP"
description = "Autoriser les connections SSH et HTTP"
rule {
from_port = 22
to_port = 22
ip_protocol = "tcp"
cidr = "0.0.0.0/0"
}
rule {
from_port = 80
to_port = 80
ip_protocol = "tcp"
cidr = "0.0.0.0/0"
}
}